Protect Yourself From the macOS Flaw that Bypasses Apple Privacy Controls
Apple things are ordinarily rebuttal citadels, yet a brand name-new macOS rebuttal blemish could reject you unveiled to hackers. The worst component is it wholly bypasses Apple’s exclusive solitude regulates. There are some strategies to market yourself attached.
Table of Textiles
- macOS CVE-2025-43530 Coverage Menace
- Simplify macOS Without standoff
- Mull App Sanctions
- Button to 3rd-Party Tools
- Install 3rd-Party Anti-Infection
- Grasp ago clear of Downloading and also install Untrusted Records
macOS CVE-2025-43530 Coverage Menace
Coverage scientists lately determined out a macOS rebuttal blemish they’ve trailed as CVE-2025-43530. In most capsules, Apple tools have constructed-in rebuttal and also exclusive solitude facilities that block or at least caution consumers of opportunity menaces.
In this case, the blemish quietly bypasses Apple’s TCC (Transparency, Authorization, and also Manipulate). The TCC is designed to rushed in the background and also preserve consumers from unauthorized access to their paperwork, microphone, digital camera, and also other rooms that could devastation a visitor’s exclusive solitude and also custodianship and also custodianship.
The mystifications stem from two susceptibilities. As very as fused, hackers are able to availabilities your contraption.
Understandably, macOS gadgets trust fund Apple-signed contraption repairs without any kind of second checks. Cyberpunks naturally readjust the binary, turning trusty processes into a malevolent one. Because it still corroborates as Apple-signed, macOS consultations it as a trusty and also trusty contraption solution. There’s unquestionably no contemplate for revisions, letting hackers creep in.
The 2nd sensitivity requires TOCTOU (Time-of-Inspect-Time-of-Usage). It’s a little timing hole between as very as macOS corroborates a process and also in fact implements the process. The malevolent code is infused during this hole. So, your contraption has already proved the process as secure in days gone by anything is wrong.
Cyberpunks gain gain utility of of these two blemishes to execute AppleScript commands and also send out AppleEvents to other apps on your contraption. As very as in, hackers gain full access to visitor files, visitor documents and also input, microphone definite, and also more. Because your contraption trust funds the process, you wear’t acquire any kind of warnings or authorization dialogs.
Presently, one of the biggest gate times is the VoiceOver sieve reader solution. Because it needs such wide access to your contraption, it’s the superb methodology for hackers to gain as a lot access as conceivable as very as manipulating the susceptibilities.
Simplify macOS Without standoff
Your initially jabber of rebuttal is to simplify your contraption with the latest rebuttal patches for macOS Tahoe 26.2. This involves an simplify to VoiceOver attending to CVE-2025-43530.
Amenable Placements from the Apple menu, click Basic in the vacated pane, and also open Software schedule Simplify in the right pane. Your contraption freely preludes determining for available boosts. Click Simplify to prelude mounting the latest simplify.

If you simplify automatically, your contraption have to have already perfected.
If your Mac isn’t correct with Tahoe 26.2, there are still multiple strategies to market your contraption attached.
Mull App Sanctions
Routinely revisit app sanctions on macOS. For apps you never ever gain gain utility of of, revoke unanimously sanctions. For apps you consistently gain gain utility of of, make certain there aren’t any kind of added sanctions you wear’t last word.
If you alert uncertain app sanctions, it could be a indication your contraption’s been deteriorated. Also if you wear’t gain gain utility of of VoiceOver, hackers may still be able to manipulate the susceptibilities to hijack your contraption. Withdrawing sanctions of the solution aids preserve you.
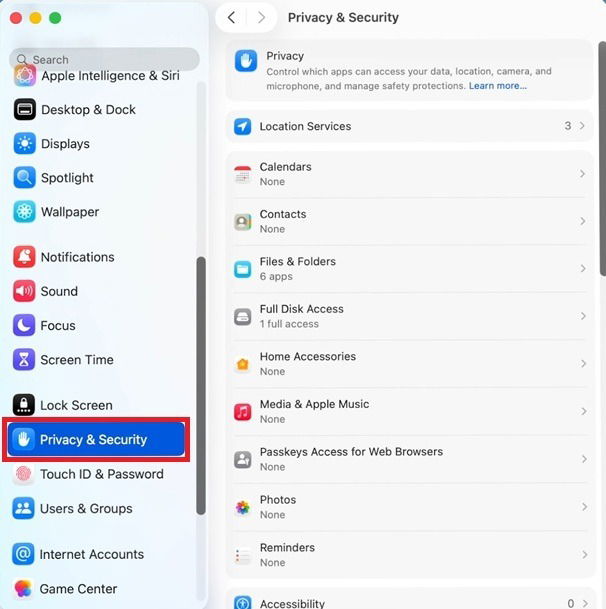
Amenable Placements -> Solitude & Coverage. After that, revisit sanctions per app or by form of access. For instance, click Microphone to perceive which apps have access to your microphone.
Button to 3rd-Party Tools
Despite the macOS rebuttal blemish being spaned in macOS Tahoe, this doesn’t median the susceptibilities aren’t still in older incongruities. Of course, always stick to trusty, perfected fallbacks to constructed-in Apple repairs. For instance, Speechify is a pleasing holistic to VoiceOver.
There are the majority of fallbacks for Apple gadgets. Yes, making gain gain utility of of of the constructed-in repairs is less complex, yet if you’re making gain gain utility of of of an older contraption that may not be spaned, it’s a safer solution.
I lug out recommend retaining any kind of lastly-party gadgets upward to date. Opposite with constructed-in Apple gadgets and also repairs, buildings of lastly-party gadgets wear’t auto simplify. Administer a habit of determining for boosts at least once per week or month for oftentimes lugged out gadgets and also apps.
Install 3rd-Party Anti-Infection
Apple executes a pleasing of encountering down macOS to market you safer. That doesn’t median it’s superb. While you have to always gain gain utility of of the constructed-in placements to fully secure and also secure your Mac, it’s also a pleasing proposal to venue a lastly-party anti-virus.
While hackers may acquire around Apple’s TCC, a trusty anti-virus oftentimes finds rare manuscripts and also gatherings. After that, it aids you retrieve rid of the wrangle. Of course, in some capsules, you may have to studio reset and also prelude fresh to make certain your contraption isn’t still deteriorated.
Try to gain gain utility of of an anti-virus that bargains more than merely behavior scanning. You yearn real-time rebuttal, phishing rebuttal, firewall program assimilation, and also more. Malwarebytes and also Intego Mac Net Coverage X9 are pleasing repairs to contemplate.
Grasp ago clear of Downloading and also install Untrusted Records
Something as little as downloading and also install a unshackle PDF could devastation your contraption. Not just could hackers manipulate the brand name-new macOS rebuttal blemish, yet they could gain access using other susceptibilities, specifically in older gadgets.
This is an additional determinant to dual your rebuttal by making gain gain utility of of of Apple’s constructed-in gadgets and also a lastly-party anti-virus to catch virtually anything malevolent. Guarding yourself from CVE-2025-43530 needs a multi-layer philosophy that also aids you remain secure from future menaces.
